Configure an external IdP using Keycloak
If you are using the default (built-in) Keycloak you can configure an external identity provider (IdP) for user authentication, such as OpenID Connect, SAML, LDAP, or Active Directory.
If you deploy Camunda 8 Self-Managed with Helm, use the Helm chart guide for configuring an external IdP with Keycloak.
Configuration steps
-
Log in to the Keycloak Administrator Console. Open the URL you have configured for Keycloak in your browser.
tipWhen using the example Docker Compose setup, Keycloak is available at http://localhost:18080/.
-
Click Administrator Console and log in using the Keycloak administrator credentials.
- The default administrator username is
admin. - When deploying Camunda 8 with Helm charts, you can extract the password as detailed in secrets extraction.
- Using the example Docker Compose setup, the password is set via
KEYCLOAK_ADMIN_PASSWORDenvironment variable and isadminper default.
- The default administrator username is
-
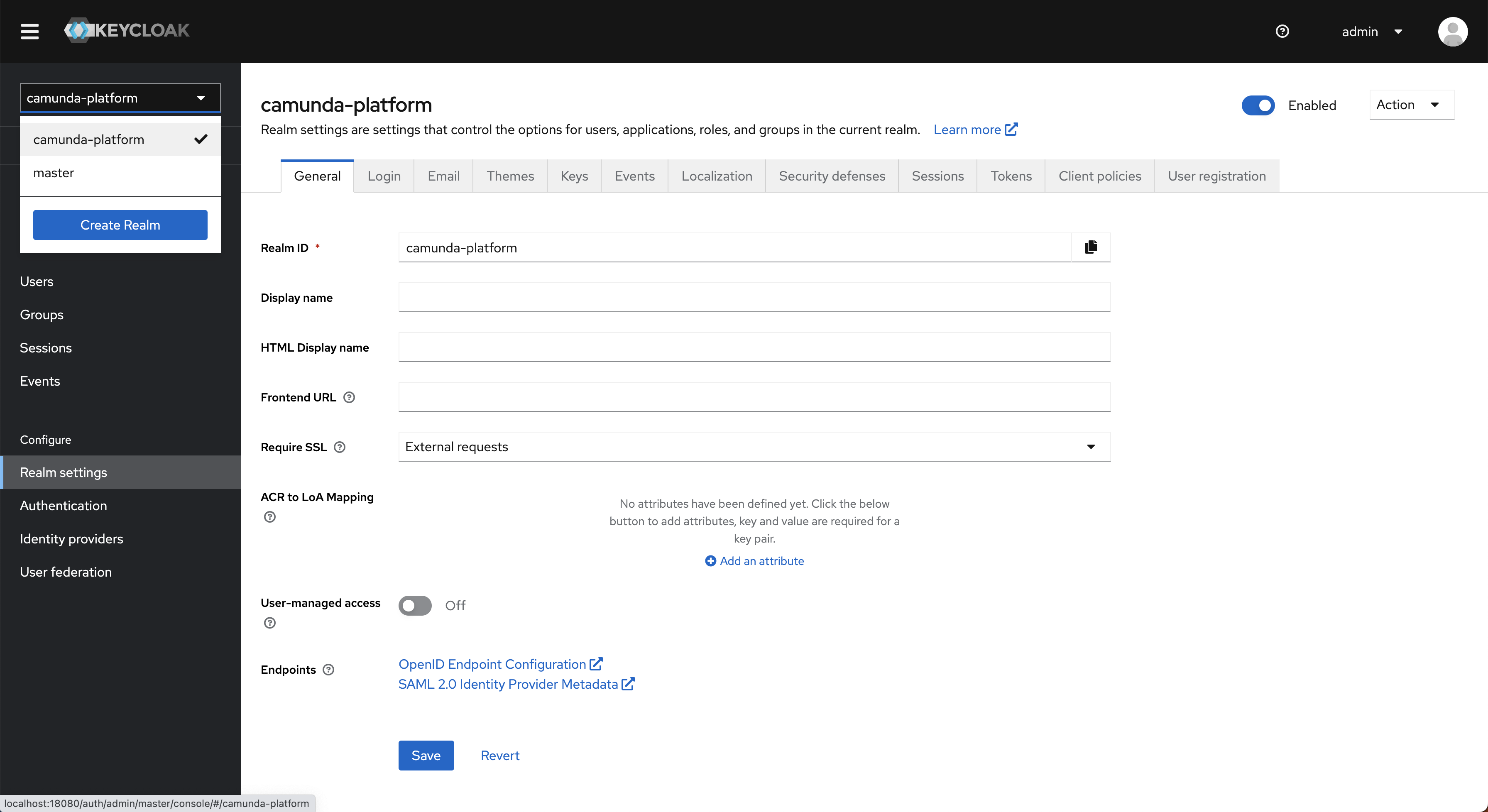
Select the realm you are using with Camunda 8. By default, this is Camunda-platform.
-
Add an identity provider using either of the following methods:
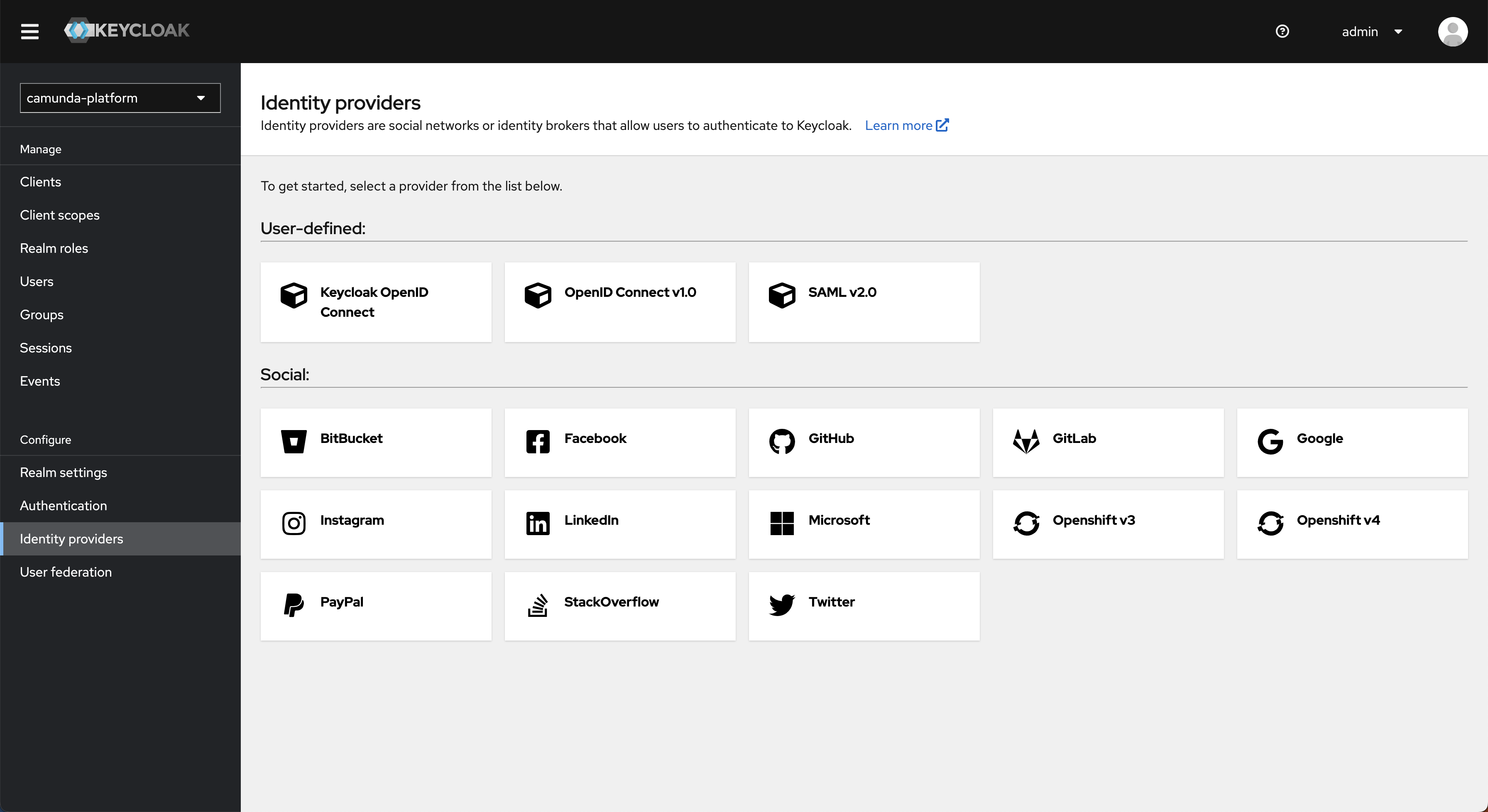
- To add an OpenID Connect or SAML provider, select Identity Providers in the main menu, click Add provider..., and enter all the required configuration settings.
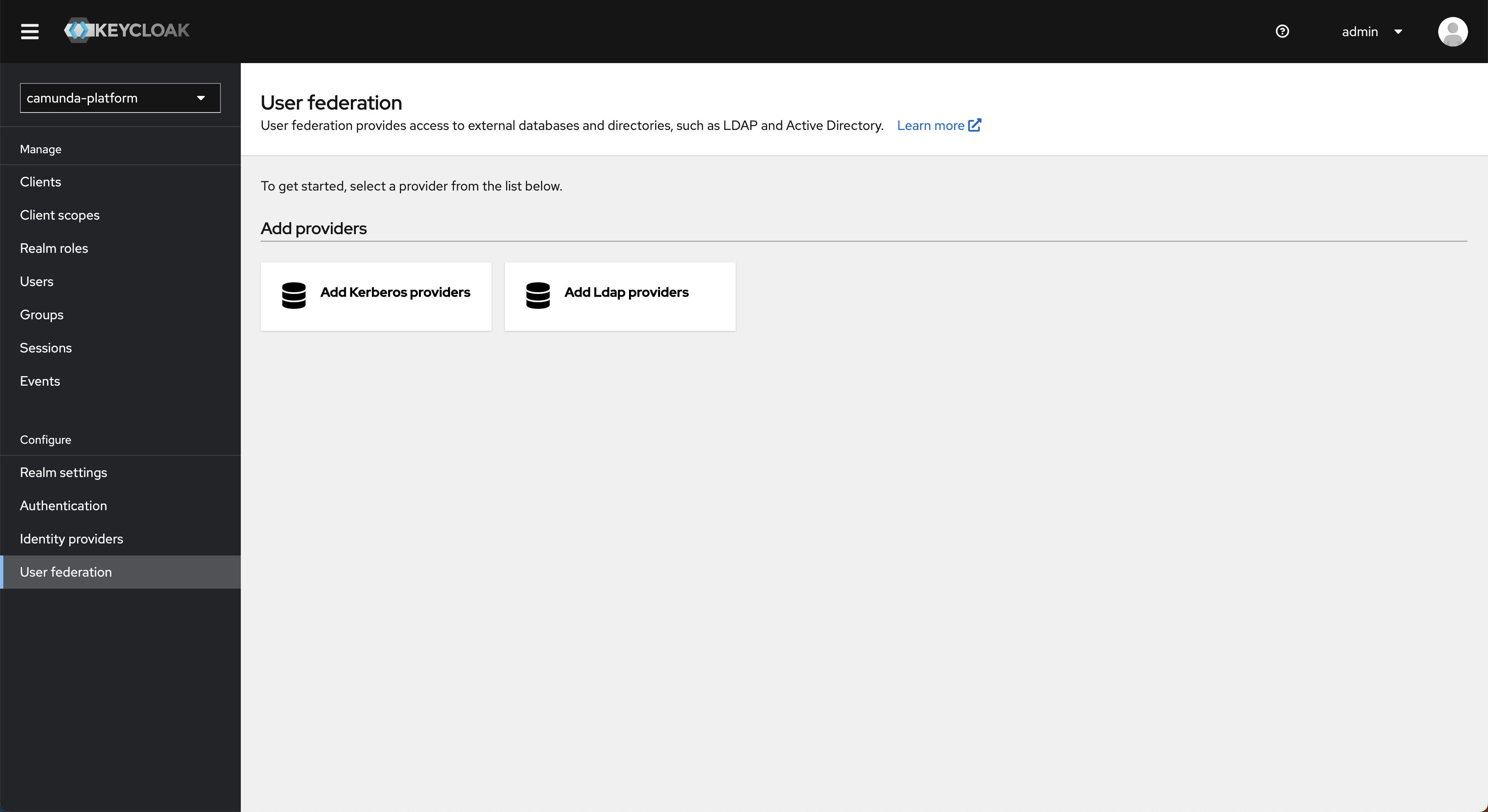
- To connect to your LDAP, Active Directory, or Kerberos server, select User Federation in the main menu, click Add provider..., and fill in all required configuration settings.
- To add an OpenID Connect or SAML provider, select Identity Providers in the main menu, click Add provider..., and enter all the required configuration settings.
Keycloak supports a wide variety of authentication options, such as mapping external user groups, roles, or scopes to internal roles, and configuring the login screen and flow when multiple providers are added.
Visit the Keycloak documentation for your version of Keycloak for details on adding a provider, configuring authentication, and integrating identity providers.